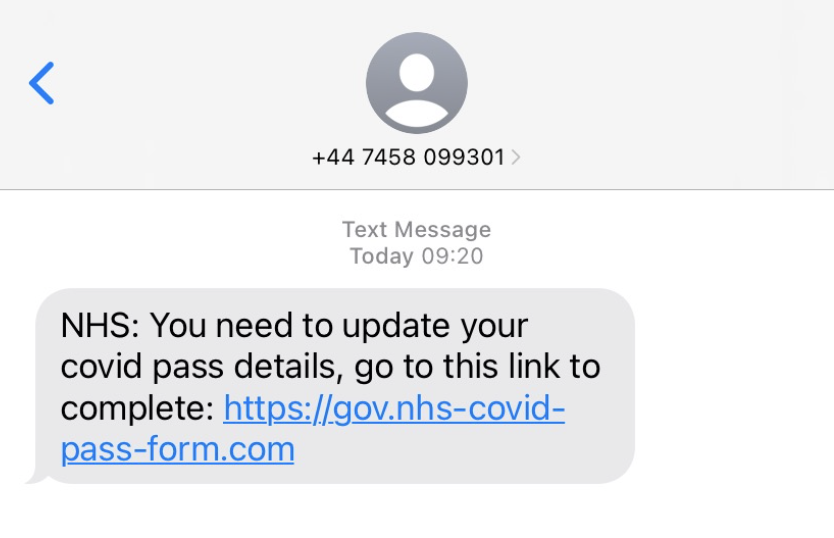
Many people are already aware of the scams that start with Smishing (SMS Phishing). For the uninitiated, this is where a malicious actor sends SMS messages to try to get a victim to click a link. They normally suggest that a payment has failed and that the victim will lose access to something unless they make a payment. The embedded links will often have similar names to the genuine site, or will be obfuscated using short links. When the victim visits the site, it’ll usually look very similar to the site the attacker is trying to impersonate. The attack will attempt to extract personal information, including name address, date of birth and also financial data such as bank details, credit/debit card numbers etc.
This morning one of my comrades received the above message. Now to me this is quite clearly a scam. I say clearly to me, but there would be plenty of non-technical folks that would fall for this. The website for the NHS is nhs.uk for starters, and they definitely don’t send SMS’s from a mobile number, so we know this must be a fake. As always the inquisitive being that I am, I tried to find out what nefarious things the threat actor was up to.
I started with urlscan.io to see what they were hosting, but I noticed that I got a redirect to the official NHS website. Okay, thats odd. Using my dirty investigations VM I pulled up a browser and changed the User Agent to one mimicking a mobile device. Still a redirect to the official site. Hmmm.
Guessing that the threat actor had put in a IP whitelist, I used a mobile IP and the fake User Agent. I finally get some traction. Whilst I no-longer get redirected, our friendly attackers have not configured their phishing website correctly.
I should point out that most of the phishing pages you see today are not written by the actors hosting them. Phish Kits, as they are referred to, are produced by a different group of people who then sell these on for others to use. As a result you find that the conmen that set-up the sites are often not especially knowledgeable about the technology they are using.
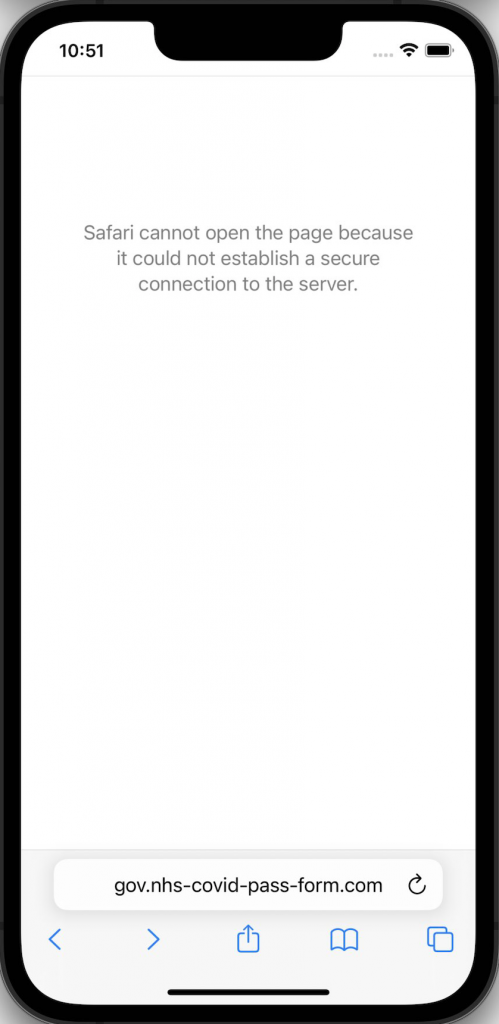
In this instance, the attacker clearly did not have the knowledge to set up their site correctly as I was unable to get to any page asking for me to enter details. Any victims clicking on the attacker link would have seen the below:
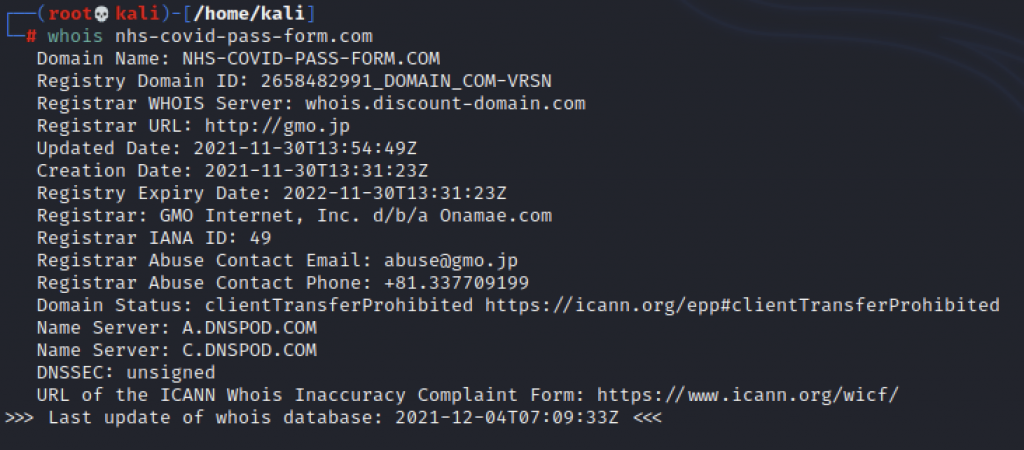
I dug into the registrar and hosting provider, and came across ones I haven’t previously noted associated with this kind of behaviour:
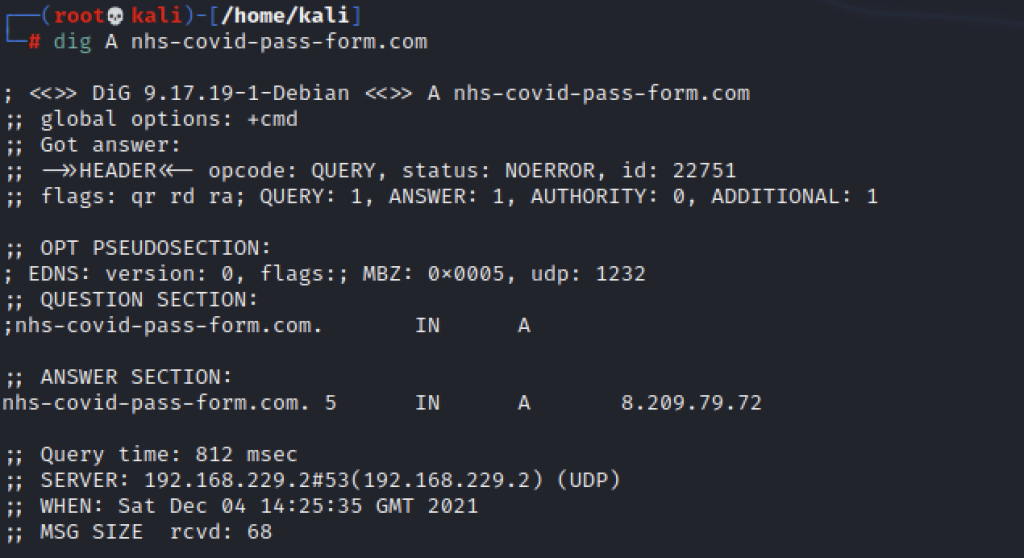
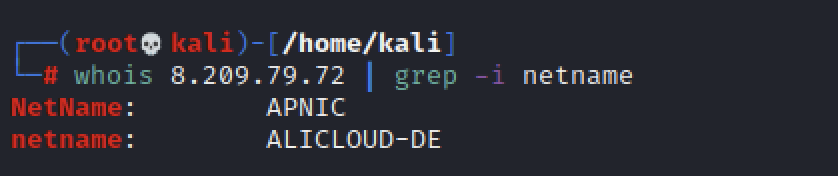
The hosting is on Alibaba’s Cloud service and at the time of publishing this article I was able to detect 21 different domains that either are, or have recently been, using this server. The domains are listed here:
1 gov-apply-passport.com
Name servers: ns2.suspended-domain.com (
) ns1.suspended-domain.com (
)
2 gov-apply-passports.com
Name servers: ns2.suspended-domain.com (
) ns1.suspended-domain.com (
)
3 gov-order-passport.com
Name servers: ns2.suspended-domain.com (
) ns1.suspended-domain.com (
)
4 gov-passport-covid.com
Name servers: ns2.suspended-domain.com (
) ns1.suspended-domain.com (
)
5 gov-passports-apply.com
Name servers: ns2.suspended-domain.com (
) ns1.suspended-domain.com (
)
6 gov-passports-covid.com
Name servers: ns2.suspended-domain.com (
) ns1.suspended-domain.com (
)
7 gov-passports-register.com
Name servers: ns2.suspended-domain.com (
) ns1.suspended-domain.com (
)
8 gov-register-passport.com
Name servers: ns2.suspended-domain.com (
) ns1.suspended-domain.com (
)
9 nhs-covid-applications.com
Name servers: a.dnspod.com (
) b.dnspod.com () c.dnspod.com ()
IPv4: 8.209.79.72 (
)
10 nhs-covid-forms.com
Name servers: a.dnspod.com (
) b.dnspod.com () c.dnspod.com ()
IPv4: 8.209.79.72 (
)
11 nhs-covid-pass-apply.com
Name servers: a.dnspod.com (
) b.dnspod.com () c.dnspod.com ()
IPv4: 8.209.79.72 (
)
12 nhs-covid-pass-form.com
Name servers: a.dnspod.com (
) b.dnspod.com () c.dnspod.com ()
IPv4: 8.209.79.72 (
)
13 nhs-covid-pass-register.com
Name servers: a.dnspod.com (
) b.dnspod.com () c.dnspod.com ()
IPv4: 8.209.79.72 (
)
14 nhs-covid-passports.com
Name servers: a.dnspod.com (
) b.dnspod.com () c.dnspod.com ()
IPv4: 8.209.79.72 (
)
15 nhs-covid-register.com
Name servers: a.dnspod.com (
) b.dnspod.com () c.dnspod.com ()
IPv4: 8.209.79.72 (
)
16 nhs-covid-verify.com
Name servers: a.dnspod.com (
) b.dnspod.com () c.dnspod.com ()
IPv4: 8.209.79.72 (
)
17 nhs-new-passport.com
Name servers: a.dnspod.com (
) b.dnspod.com () c.dnspod.com ()
IPv4: 8.209.79.72 (
)
18 nhs-register-covid-pass.com
Name servers: a.dnspod.com (
) b.dnspod.com () c.dnspod.com ()
IPv4: 8.209.79.72 (
)
19 nhs-register-pass-covid.com
Name servers: a.dnspod.com (
) b.dnspod.com () c.dnspod.com ()
IPv4: 8.209.79.72 (
)
20 nhs-register-passport.com
Name servers: a.dnspod.com (
) b.dnspod.com () c.dnspod.com ()
IPv4: 8.209.79.72 (
)
21 nhs-register-passports.com
Name servers: a.dnspod.com (
) b.dnspod.com () c.dnspod.com ()
IPv4: 8.209.79.72 () You can see that this threat actor is focusing in on NHS Covid scams in particular. The reason for choosing this type of attack are that they are usually fairly effective, especially since banks and mobile networks have implemented a number of mechanisms to protect their users, including 2FA and additional checks.
If you are a regular user I’d highly recommend against attempting to do your own investigation into these scammers. As I’ve stated on this post, and some previous ones, the payload that is delivered can be varied based on a variety of factors – this can include your IP, User Agent and a number of other things. In investigations we’ve seen how the payload can even vary depending on the number of times a location has been visited. The risk that you take is that unusual/previously unseen malware will make its way onto your machine.
My advice is: do not visit any link sent over SMS unless you are 100% sure it is genuine. If you have even the smallest doubt at all, reach out to the company directly by visiting their official website and using the contact information you find on that page.
If there is one take-away here, it’s that checking a site using online tools does not guarantee it’s safe.
Many people are eagerly awaiting a bonus at Christmas time, scammers are looking for one too. Don’t be their pay day.