I didn’t have much time to take on the challenges in this CTF, and as a team of one, my chances of doing much were pretty limited. That said, I was going to use what time I had to give it go.
The opening challenge involved connecting to a port on a public system. And this is what I got:
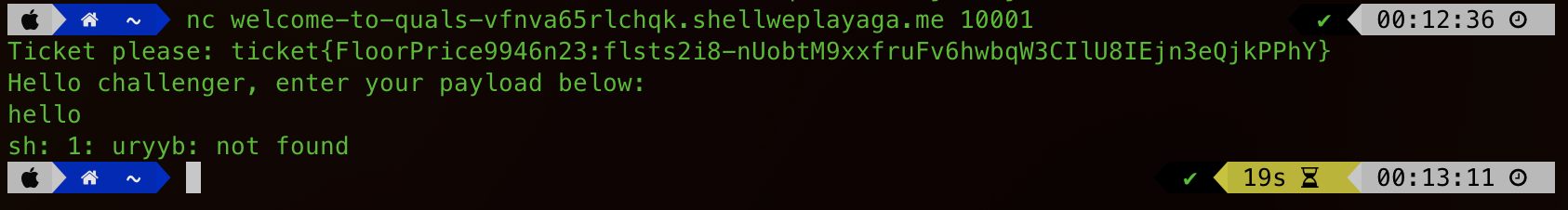
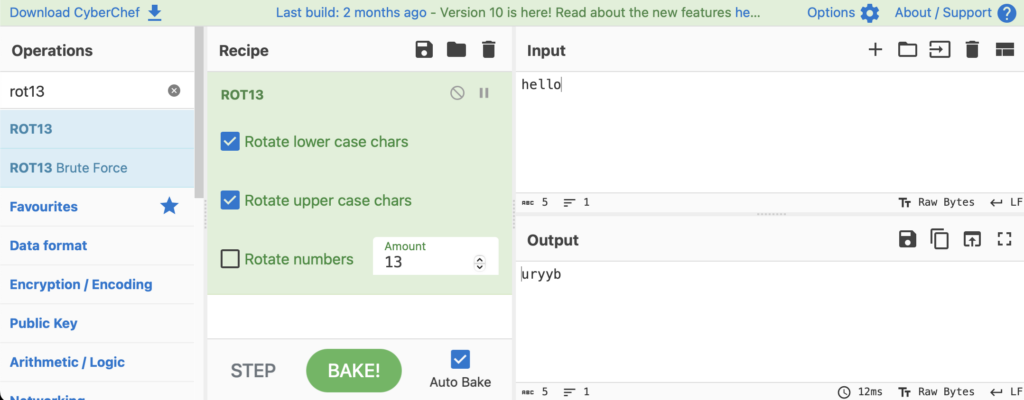
It’s funny how just a tiny amount of information can give the game away. I typed “hello” and the response of “uryyb” immediately had me thinking ROT13. A quick trip to Cyber Chef later and this had been confirmed.
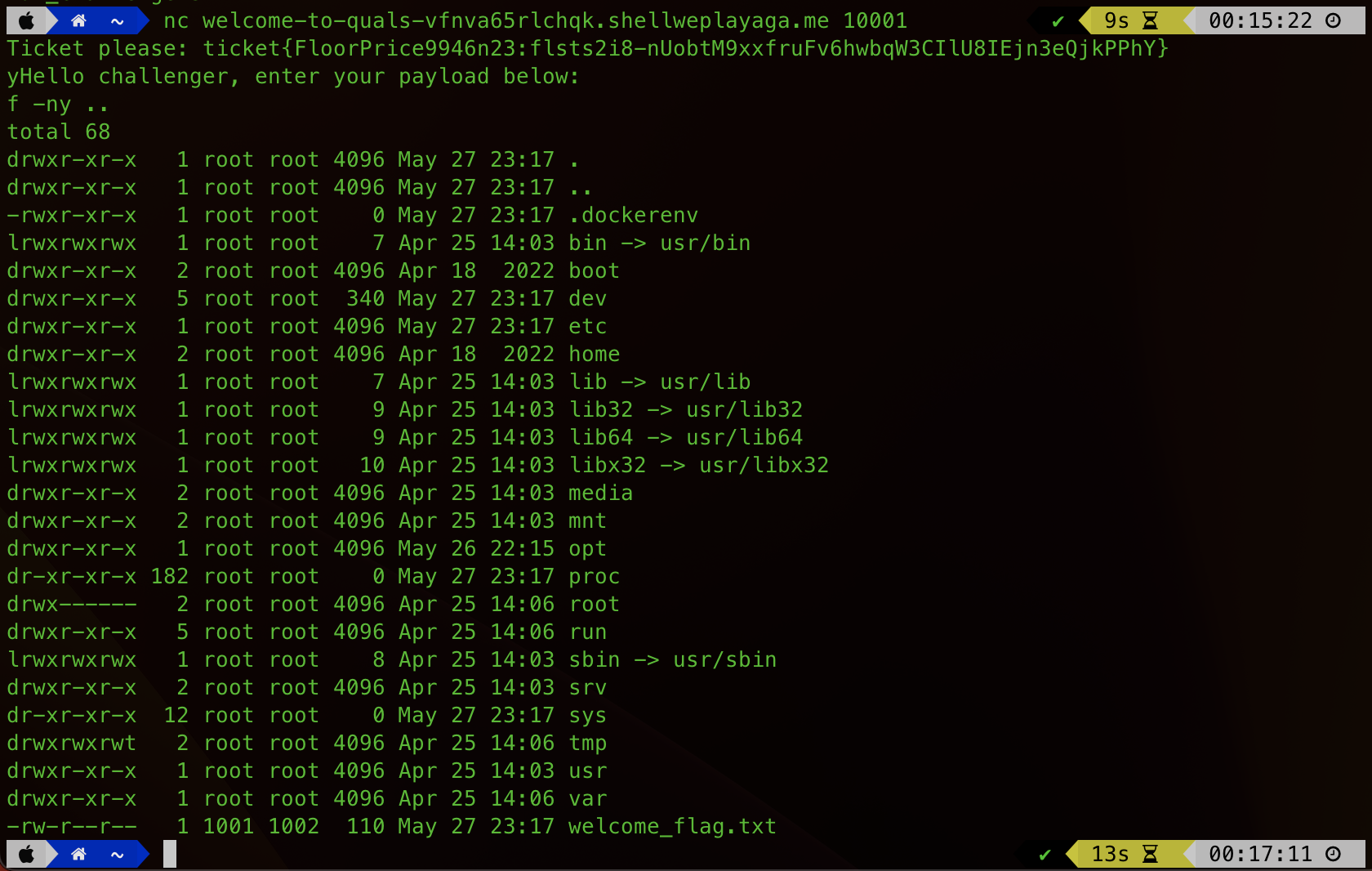
As we now know the “encryption”, we can try running some unix commands. I started off with ls. Which translated into “yf”:
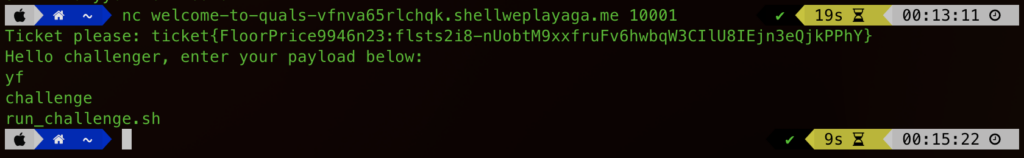
Awesome. So we’re just dropped onto the filesystem and can run commands. At this point I went wildly off the rails and was trying to get a shell back. I’m not actually sure why I tried. But try I did. After a while I realised that this was not only pointless, but the challenge was much simpler. I did a list of the parent directory and it immediately was obvious what I needed to do.
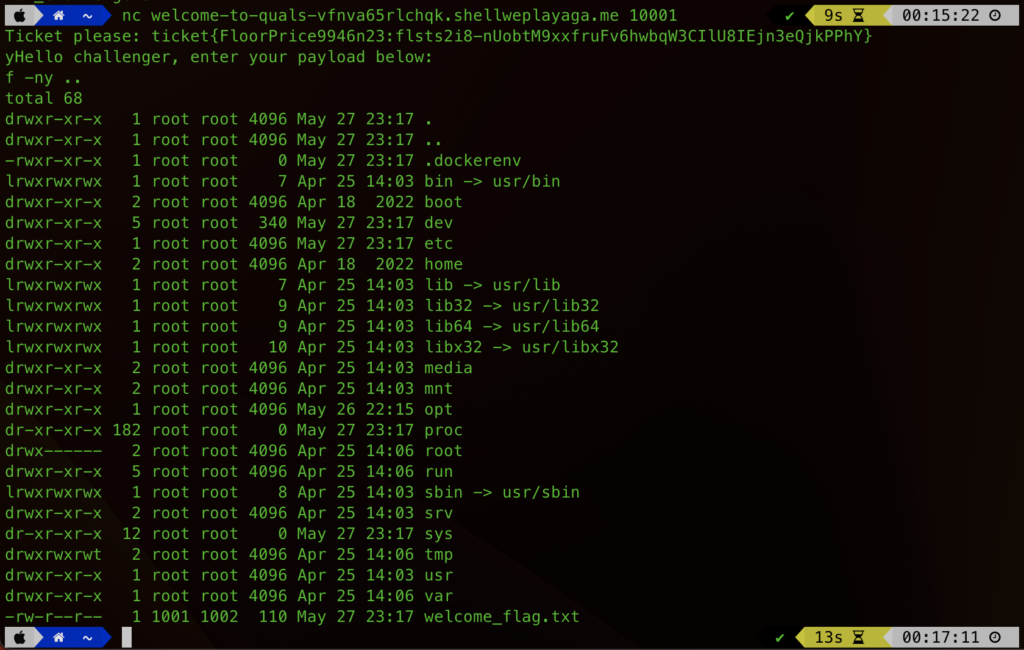
With the subtlety of a spanner in the face, welcome_flag.txt was revealed and laughing at me for my futile attempts to get a shell. All we needed to do was display the file…
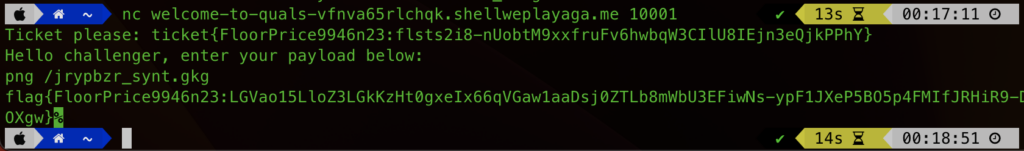
Just like that we were done. With unfortunately no more time to spend, this was the only challenge I really gave any effort to. I don’t think I’ll be entering the DEF CON CTF on my own any time soon…