Over the years I’ve run quite a few different websites. Most of them have ended up in Internet dustbin but now and again there is content I want to preserve. Recently I pulled a site from a server that was so old it’d begun making trips to Bournemouth and getting itself a blue rinse.
I had a shiny new platform to host this old site and went through the usual motions of securing it including patching it through Cloudflare. As well as helping protect and speed up the site, Cloudflare also offer Certificate Transparency reporting. This valuable service identifies if a certificate has been created for my domain and then emails me about the detail of said certificate. Should an attacker compromise the domain in some way and create a certificate, this notification will alert me to take action.
Given that this was a low value domain, on a site that probably only gets stumbled upon half a dozen times a year, it’s not high on the list for an attacker to take-over. However, when an email came in from the CT service that a new certificate had been created alarm bells started ringing.
The mail said that a new certificate had been issued by Google Trust Services. The problem is: I don’t use Google Trust Services. Time to do some investigation.
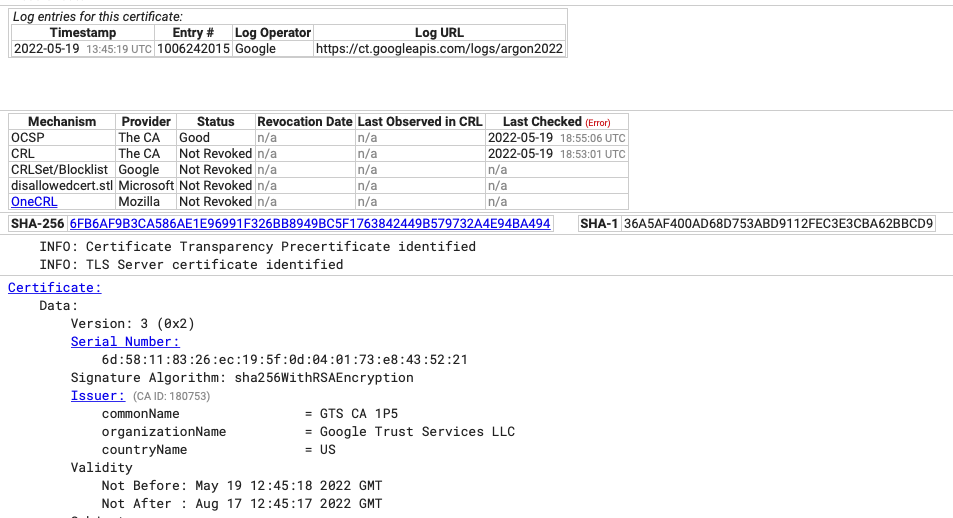
My first stop was to https://crt.sh which allows you to see all of the certificates issued to any domain. Checking on the domain in question, I saw the last entry was a wildcard cart generated by the GTS CA. I wondered if Certbot on the server (responsible for managing the TLS certificate for my site) had requested the certificate and, for reasons unknown, ended up with one from Google.
Each certificate has a serial number that allows you to quickly identify them. In the image above taken from crt.sh it’s easy to find this. We can check the certs on my server to see if it has a matching serial.
openssl x509 -noout -serial -in cert.pem | cut -d'=' -f2 | sed 's/../&:/g;s/:$//'This command examines the certificate and outputs its serial in a pretty way on the console for us to do a comparison. It was not surprising to see that none of the serial numbers matched. Given that I clearly didn’t ask for this to be issued, I took the next step. I needed to chat with the issuer and usefully crt.sh have a link on each entry which gives you the contact details of the issuing CA.
Credit to Google’s CA team. They came back very quickly with the detail explaining that the certificate was issued to Cloudflare. Immediately that put my mind at ease. They went further and explained why Cloudflare (who is a CA themselves) were being issued with a Google certificate. Its a new service! You can find out more about the feature here: https://blog.cloudflare.com/introducing-backup-certificates/
My mind: finally at peace.
I advise anyone who has a domain to protect to ensure you are receiving the relevant CT reports. Cloudflare offer the service for absolutely free and other providers can offer this gratis too.
On this occasion it turned out that I need not worry, but it served as useful exercise in what to do in the event the alarm sounds.