I have exactly one write-up for this CTF. The challenge chosen was a Fullpwn, specifically a machine called Volnaya. An enumeration of the machine with nmap reveals port 22 offering SSH services, and port 80 with an nginx web service. A peek at the web site showed nothing of any […]
About: dg
- Website
- http://davidguest.uk
Posts by dg:
Return to libc
I’ve been playing around with a selection of fun reversing tooling recently and thought it might be fun to go through a basic challenge to escalate privileges via a vulnerable executable. The first tool we’re going to use is gdb but we’re going to extend its capabilities significantly with pwndbg. […]
HTB Business CTF 2023: Langmon
HTB Business CTF 2023: Lazy Ballot
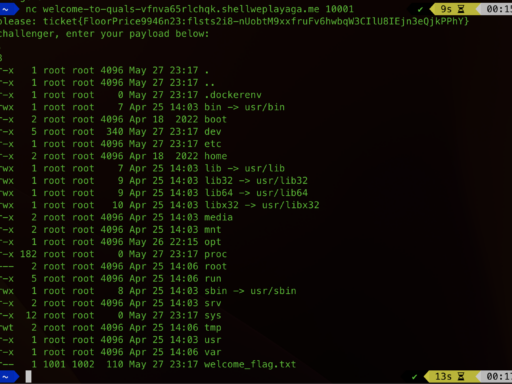
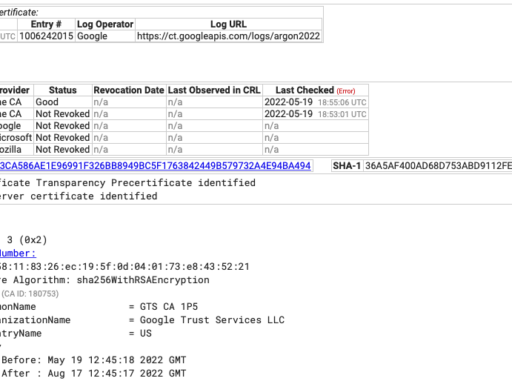
DEF CON CTF 2023 Qualifiers: Challenge 1
Using DFSCoerce to fully pwn a domain
Last year, vulnerabilities were discovered in Windows which – using Microsoft’s Encrypting File System Remote Protocol (MS-EFSR) – allowed exploitation via Active Directory Certificate Services (AD CS). Whilst Microsoft provided patches which prevented the original PetitPotam attack, another called ShadowCoerce used a different endpoint and allowed a similar route to […]