Illumination, a 20 point Hack the Box forensics challenge, asks the question “can you find the secret token?”. The back story is that a Junior Developer has just switched to a different source control platform.
Theres a ZIP file to download, as with most of these challenges, which when inflated contains two regular files and a hidden .git directory. Most of those living in the shadows are very used to typing git clone to pull the latest interesting tool on GitHub. However, maybe we’re all not so familiar with git version control tooling? This challenge will sort that out.
The two regular files are bot.js and config.json. One of those is promising straight away.
└─# cat config.json
{
"token": "Replace me with token when in use! Security Risk!",
"prefix": "~",
"lightNum": "1337",
"username": "UmVkIEhlcnJpbmcsIHJlYWQgdGhlIEpTIGNhcmVmdWxseQ==",
"host": "127.0.0.1"
} For fun I had a look at what the base64 encoded username was:
echo UmVkIEhlcnJpbmcsIHJlYWQgdGhlIEpTIGNhcmVmdWxseQ== | base64 -d
Red Herring, read the JS carefully I did have a look at the JS – but honestly it wasn’t going to reveal anything more than I already knew: the token field in the json was the interesting part. Lets have a look at the commit history for this project:
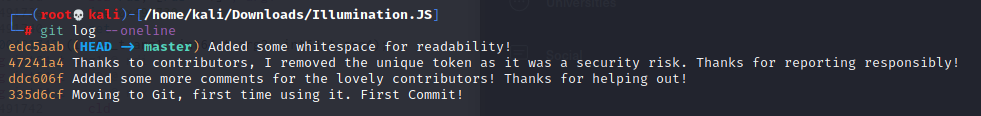
Okay – so we have compelling evidence here that an early commit removed the security token. I thought that a git revert would allow me to roll this project back to a point where the token would be present. It didn’t though. So I went poking a little deeper. In the .git/logs directory there is a file called HEAD which contains details of the commits.
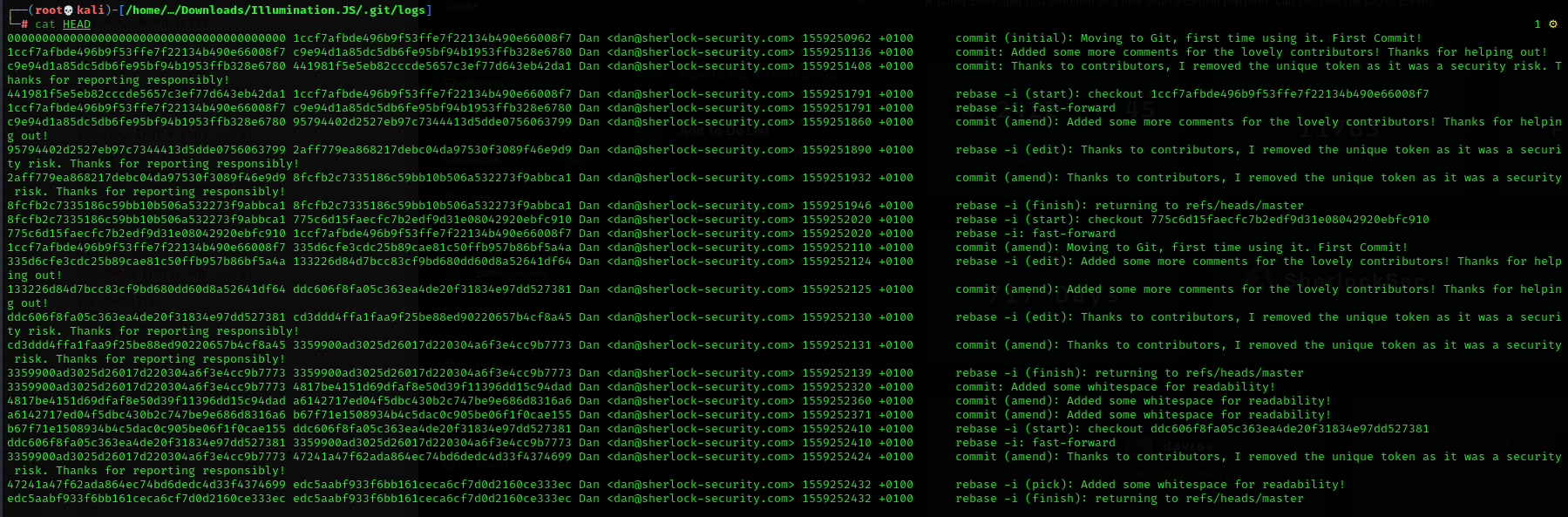
You can use git cat-file -p <object> to examine the files that make up the git structure. I used this to look at one of the early commits.
└─# git cat-file -p 1ccf7afbde496b9f53ffe7f22134b490e66008f7
tree 3051d4746a51f549ea82c72c6a23db3fbbd33c6a
author Dan <[email protected]> 1559250962 +0100
committer Dan <[email protected]> 1559250962 +0100
Moving to Git, first time using it. First Commit!
Theres a tree object listed in this file. This is going to contain detail of the modified files and can be treated in the same way – rinse and repeat:
└─# git cat-file -p 3051d4746a51f549ea82c72c6a23db3fbbd33c6a
100644 blob 7eb834acc2350f020aa94cbd2f3f54767605fbfb bot.js
100644 blob 316dc217bceb0ca5bfdfa814c18e60ac833620b6 config.json
We already ascertained that it’s config.json that holds the key. Literally. So let’s look at that. Can you guess how you do that?
└─# git cat-file -p 316dc217bceb0ca5bfdfa814c18e60ac833620b6
{
"token": "SFRCe3YzcnNpMG5fYzBudHIwbF9hbV9JX3JpZ2h0P30=",
"prefix": "~",
"lightNum": "1337",
"username": "UmVkIEhlcnJpbmcsIHJlYWQgdGhlIEpTIGNhcmVmdWxseQ==",
"host": "127.0.0.1"
}Given that this is a 20 point challenge, I think we can safely assume we’re not going to need any Cyber Chef treatment – and indeed the token is our flag that has been base64 encoded.
Not one thats going to be tricky for most but a useful exploration of git tooling all the same.
