Shoppers of Angling Direct were in for a bit of a surprise recently if they navigated to the fishing stores website. Instead of being able to review the latest equipment to catch a big fish, they were directed to a well known pornography website.
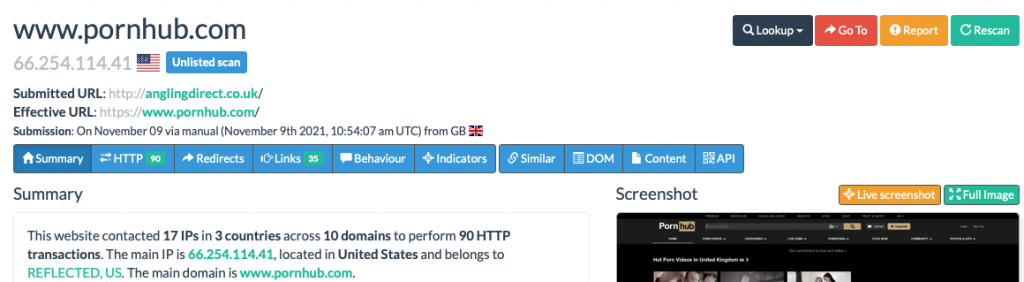
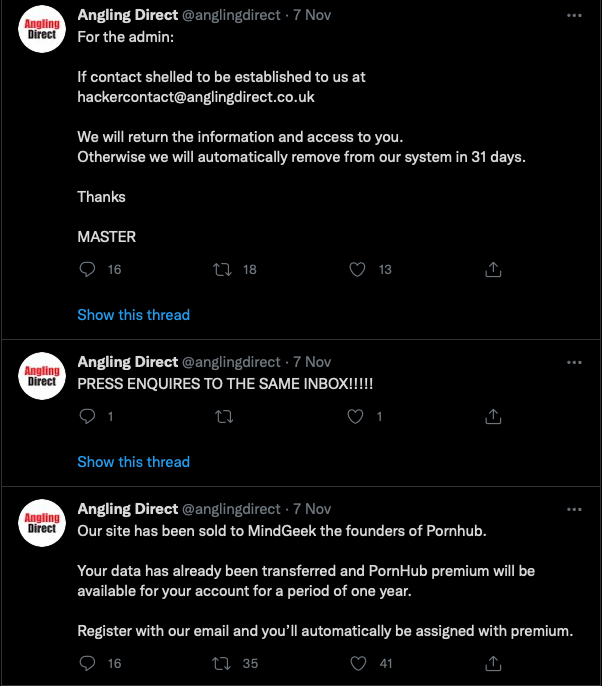
Checking their social media it, and we find that has been compromised too. So how has this happened? Did an attacker really get all of the passwords needed through a single hack?
There’s clear evidence that this wasn’t actually a website take-over. At least not initially. It’s likely to be every engineers favourite: DNS.
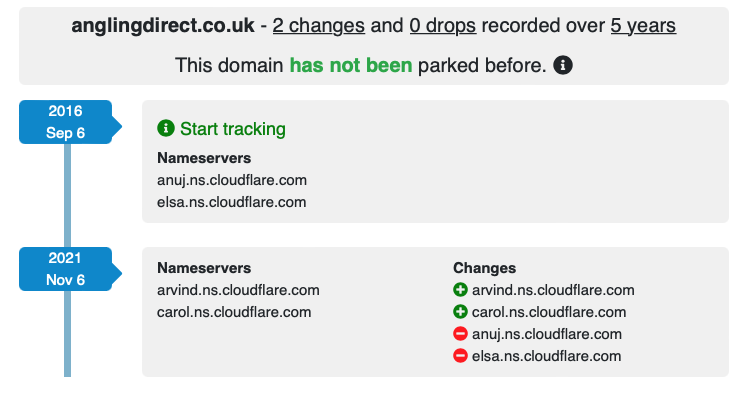
Sometime on 6th November it seems that an attacker gained access to Angling Direct’s GoDaddy account (ironically that was probably via Phishing!). This almost certainly means that MFA had not been used. Unlike a website compromise where an attacker uses a vulnerability in the web application to gain access to deface pages – this is far more serious.
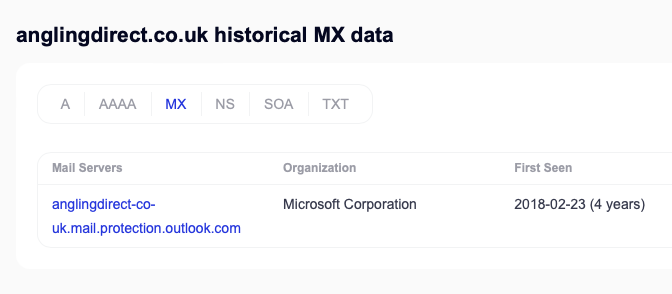
Once the attacker had compromised GoDaddy, they then changed the NS records to point to the malicious actors own Cloudflare account, changed the A records to point to PornHub, and proceeded to change where emails were being sent by altering the MX records. As a result they were then able to takeover all of Angling Direct’s external accounts – including Twitter – by simply requesting password resets. Instead of the reset emails going to Angling Direct’s M365/Exchange Online tenancy, they end up going an attacker controlled mailbox in ProtonMail.
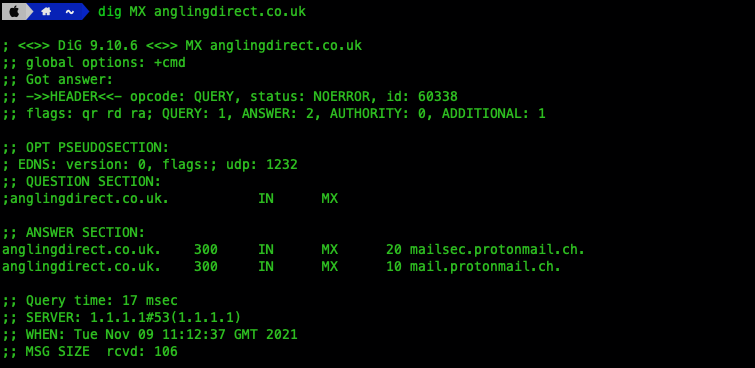
As a side-note: there’s a non-zero risk to the attacker here, if they haven’t been extremely careful. ProtonMail, whilst operating an anonymous service, have recently been compelled by a court to provide IP addresses of users. The service being used for this hack is an at-cost product too. That increases the chances of being identified – even if the attacker paid with BitCoin. If any connections to ProtonMail weren’t over TOR or similar, they could end up being tracked down and prosecuted.
What happens next will be down to how quickly Angling Direct can regain control of their DNS records. Once they do, they’ll need to implement a strong password and, importantly, something that was not in-place before: MFA. It’s likely that Angling Direct will have also lost control of their CloudFlare account and passwords for this service will need changing too. Again MFA needs implementing if they haven’t already.
They’ll need change their MX records to point back to Office365. But here be dragons. The attacker may well have compromised the entirety of the M365 tenancy. Along with exfiltration of data, they would have been able to add accounts, change passwords, implement forwarding rules, or any number of other things to dig-in and maintain persistence. This will need expert attention, a regular IT person could miss techniques that a sophisticated actor may have used.
Of course they’ll want to regain access to their social media accounts. If an attacker has implemented MFA for themselves that could take a long time, as it’ll mean direct liaison with the providers and will not be instantaneous. There might well be other problems more serious than not having access to Twitter though.
The website previously appears to have been hosted in AWS. I suspect the attacker therefore has complete control of this by now. A lot of care will need to be taken to ensure a thorough and complete eviction from the subscription. It would be so easy to overlook a permission that the attacker may have assigned themselves through IAM. A complete audit of this service is essential.
Other worries include who do they take payments from? Has the attacker been able to compromise personal details? That will land the company in trouble with the regulator, the ICO, and fines might be on the way.
Companies that have been working with Angling Direct will need to take precautions too. It’s fair to say any email from 6th onwards is untrustworthy. There’s no telling what a malicious actor may do with the access they have, so assume the worst.
How could this have been prevented? Simply: MFA – Multi-Factor Authentication. Without it, all that is protecting an account is a single password. A password that may be guessed, brute-forced, or phished. By having multi-factor authentication in place for all systems and services the chances of compromise are vastly reduced. Not having MFA for your domain hosting provider in 2021 is practically suicidal. Losing control of a domain will almost inevitably lead to loss of control of email services. Once that has happened, all bets are off. A malicious attacker can do just about anything.
If you still haven’t implemented MFA for your domain and/or your email – do it now. I mean right now. Don’t wait to become the next victim.
A final word of warning. The website anglingdirect.co.uk might only be forwarding to another domain right now, but I recommend against directly browsing to this URL. The attacker could, at any time, change his tactics and decide to place malware along the way. It wouldn’t be the first time that sort of thing has happened. Stay safe!

Well written piece.