I started this off with some very standard enumeration, getting nmap and dirbuster up and running. There was clearly something web-like and interesting running on 5000/tcp but that wasn’t accessible from an external address. Also of interest was a reference that nmap discovered to ‘staging.love.htb’. It took me longer than I’d like to admit to realise that the server had another vhost.
Adding this entry to the hosts file allowed me to see what was apparently a “malware scanner” which allowed the upload of files for them to be “checked”. After some unsuccessful attempts to get a shell, and noting that the page was echo-ing back file contents, I had a look at what SSRF I might be able to achieve. Sure enough I was able to get that interesting web-page running on 5000/tcp to load.
This isn’t a hugely uncommon misconfiguration and what it was hiding – well, I’ve seen that too: a password database. Just because you think a database can’t be accessed because it’s bound to 127.0.0.1 doesn’t mean there aren’t other ways to get to it.
Using the credentials I found I went back to the main site, but added “/admin” as my earlier enumeration had turned up. Sure enough I was straight in. The web application I could now access allowed the upload of photos. Surely I can’t just upload a php webshell? Oh, yes I can.
Obviously one desires more than a webshell, and so I uploaded a Windows version of netcat and used that to get myself a reverse shell. At this point I grabbed the user.txt flag.
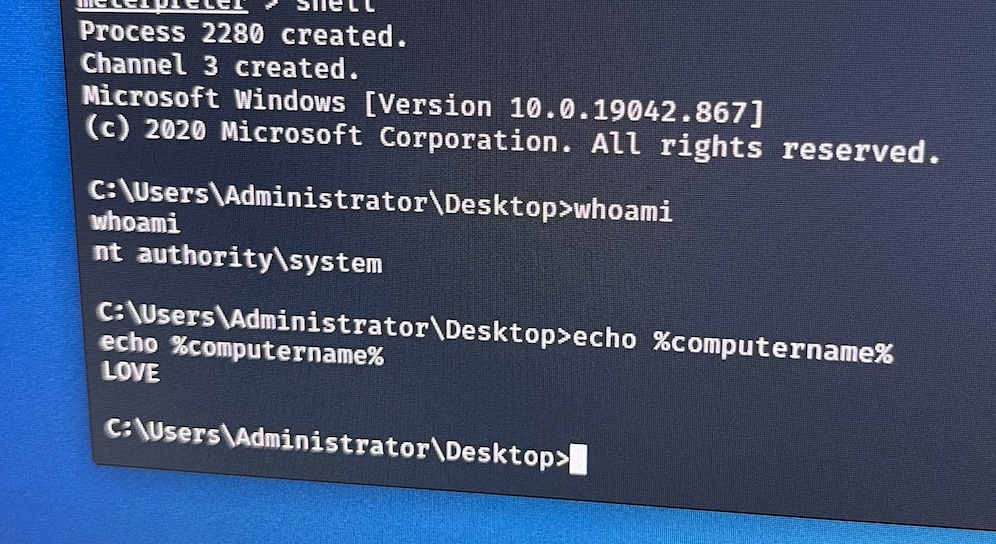
After a little more prodding I wanted to upgrade my shell some more as I wasn’t getting what I needed from my current one. Using msfvenom I created a reverse shell package and let Metasploit grant me a Meterpreter session. Thats much better.
Some more enumeration by way of WinPEAS to see what privilege escalation might be open to me. Thanks to this page: https://www.hackingarticles.in/windows-privilege-escalation-alwaysinstallelevated/ for talking in detail about naughty things you can do with MSI files, and checking a couple of registry keys – it became apparent rooting this box was going to be very simple.
Windows can, and often is, configured to allow lowly users to install software on their machines. If the box is also configured to install MSI’s with elevated permissions (i.e. SYSTEM) – then there is an easy route for Privilege Escalation.
Metasploit has a package especially for us: windows/local/always_install_elevated. Piggybacking off of the session we had earlier it look seconds to get full control.